DeviceLock Endpoint DLP Suite - CS Magazine 5 star review - To view click here
DeviceLock Endpoint DLP Suite:
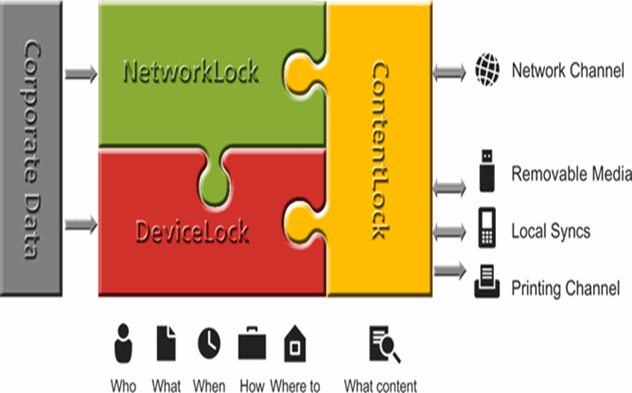
Prevent Devastating Data Leaks by Securing the Endpoints of Your Network
The Endpoint DLP Suite consists of three software modules that protect your organisation from three general categories of data leak threats:
DeviceLock provides network administrators the ability to set and enforce contextual policies for how, when, where to, and by whom data can or can’t be moved to or from company laptops or desktop PCs via devices like phones, digital cameras, USB sticks, CD/DVD-R, tablets, printers or MP3 players. In addition, policies can be set and enforced for copy operations via the Windows Clipboard, as well as screenshot operations on the endpoint computer.
NetworkLock adds contextual-level control of user network communications via the Internet through such means as: company email, personal webmail, instant messaging services, social networks (like Facebook, Google+, Twitter), web surfing, FTP file transfers, as well as cloud-based file sharing services like Dropbox, SkyDrive and Google Drive.
ContentLock adds the capability to look inside files and other data objects (like emails and web-mails, chats, blog posts, etc.) for sensitive information like social security numbers, credit card numbers, bank account numbers or other user-definable information and to make block-or-allow decisions based on policies having to do with file contents.
The combination of all three of these modules working together is the DeviceLock Endpoint DLP Suite. The Endpoint DLP Suite provides protection against local and network data leaks at the endpoint (laptop, desktop or server) via a wide array of threat vectors.
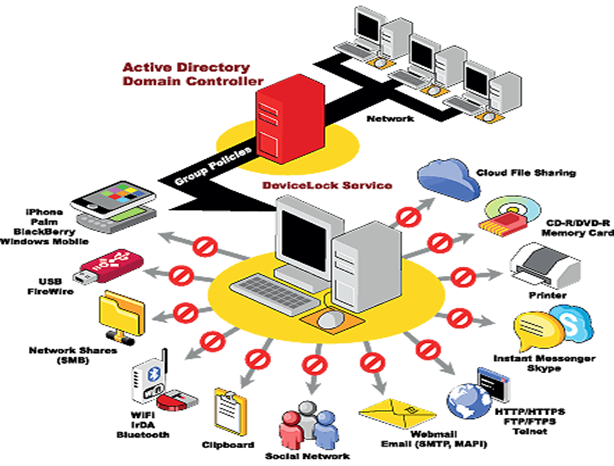
These include: iPhones, Androids, BlackBerry, other smart-phones, iPods, iPads, digital cameras, Wi-Fi, Bluetooth, FireWire, social media, IM, webmail, company email, printing, CD or DVD ROM, USB flash drives, Compact Flash, FTP/FTPS, HTTP/HTTPS and the clipboard.
Natively integrated with Microsoft Active Directory Group Policy, the DeviceLock DLP Suite is very easy and straight-forward to install and configure. Typical installations are handled by Microsoft Network Administrators and do not require expensive, specially trained resources.
The other great customer benefit of DeviceLock’s tight integration with Active Directory is that it gives the solution virtually limitless scalability. The DeviceLock Endpoint DLP Suite can effortlessly run on every endpoint listed in your Active Directory database even if there are tens of thousands.
Features of the DeviceLock Endpoint DLP Suite:
Devices Access Control: Administrators can control which users or groups can access USB, FireWire, Infrared, COM and LPT ports; WiFi and Bluetooth adapters; any type of printer, including local, network and virtual printers; Windows Mobile, BlackBerry, iPhone and Palm OS-based PDAs and smartphones; Terminal Services devices; as well as DVD/BD/CD-ROMs, floppy drives, and other removable and Plug-and-Play devices. It's possible to set devices in read-only mode and control access to them depending on the time of day and day of the week.
Network Communications Control: NetworkLock's detection technology is port-independent and recognizes network applications types and protocols where data leakage can occur. NetworkLock can be configured to control web mail, social networking communications, instant messaging, file transfer operations and Telnet sessions. NetworkLock can intercept, inspect and control plain and SSL-tunnelled SMTP email communications with messages and attachments controlled separately, as well as web access and other HTTP-based applications and encrypted HTTPS sessions. Messages and sessions are reconstructed with file, data and parameter information extracted and then passed to the ContentLock module for content filtering. Audit (event) logging and data shadowing trails are maintained as conditionally specified.
Content Filtering: ContentLock supports content filtering for data objects copied to removable drives, other Plug-n-Play storage devices, sent to printers, and through network communications secured by the NetworkLock module on the endpoint. Recognizing more than 80 file formats and data types, ContentLock extracts and filters the content of files and other data object types including emails, instant messages, web forms, social network exchanges, etc. ContentLock filters data streams based on desired Regular Expression (RegExp) patterns, numerical conditioning and Boolean combinations of “AND/OR” criteria matching. Over 50 contextual parameters can be used. These include users, computers, groups, ports, interfaces, devices, data channels, types, data flow directions, day/time boundaries, etc.
Tamper Protection: Configurable DeviceLock Administrators feature prevents anyone from tampering with DeviceLock settings locally, even users that have local PC system administration privileges. With this feature activated, only designated DeviceLock security administrators working from a DeviceLock console or GPO can install/uninstall the program or edit DeviceLock policies.
AD Integration: DeviceLock’s most popular console integrates directly with the Microsoft Management Console (MMC) Active Directory (AD) Group Policy platform. As Group Policy and MMC-style interfaces are common knowledge for Microsoft administrators, there really is no proprietary interface to learn or appliance to buy to effectively manage endpoints centrally. The simple presence of the DeviceLock MMC console on a Group Policy administrator’s computer allows for direct integration into the Group Policy Management Console (GPMC) or the Active Directory Users & Computers (ADUC) console with absolutely zero scripts, ADO templates, or schema changes. Security administrators can dynamically manage endpoint data leakage and auditing settings right along with other Group Policy–related tasks. In addition to the MMC snap-in console for Group Policy, DeviceLock also has traditional administrative consoles that can centrally manage any AD, LDAP, or workgroup network of Windows computers. XML-based policy templates can be shared across all DeviceLock consoles as well.
True File Type Control: Administrators can selectively grant or deny access to over 4,000 specific file types for removable media. When a file type policy is configured, DeviceLock will look into a file’s binary content to determine its true type (regardless of file name and extension) and enforce control and shadowing actions per the applied policy. For flexibility, Content-Aware Rules for file types can be defined on a per-user or per-group basis at the device/protocol type layer. True file type rules can also apply to pre-filtering of shadow copies to reduce the volume of captured data.
Clipboard Control: DeviceLock enables security administrators to effectively block data leaks at their very embryonic stage — when users deliberately or accidentally transfer unauthorized data between different applications and documents on their computer through clipboard mechanisms available in Windows operating systems. Copy and Paste operations can be selectively filtered for data exchanges between different applications (e.g. from Word to Excel or OpenOffice). At the context level, DeviceLock supports the ability to selectively control user access to data objects of various types copied into the clipboard including files, textual data, images, audio fragments (like recordings captured by Windows Sound Recorder), and data of unidentified types. Screenshot operations can be blocked for specific users at specific computers including Windows’ PrintScreen function, as well as screenshot operations of third-party applications.
USB White List: Allows you to authorize a specific model of device to access the USB port, while locking out all others. You can even "White List" a single, unique device, while locking out all other devices of the same brand and model, as long as the device manufacturer has supplied a suitable unique identifier, such as a serial number.
Media White List: Allows you to authorize access to specific DVD/BD/CD-ROM disks, uniquely identified by data signature, even when DeviceLock has otherwise blocked the DVD/BD/CD-ROM drive. A convenience when DVD/BD/CD-ROM disks are routinely used for the distribution of new software or instruction manuals, Media White Listing can also specify allowed users and groups, so that only authorized users are able to access the contents of the DVD, Blu-ray or CD-ROM.
Temporary White List: Allows granting temporary access to a USB-connected device by the issuing of an access code, rather than through regular DeviceLock permission setting/editing procedures. Useful when permissions need to be granted and the system administrator has no network connection; for example, in the exceptional case of accommodating a sales manager who calls in with a request for USB access when working outside the company's network.
Protocols White List: Allows you to specify whitelist-oriented policies by IP address, address range, subnet masks, network ports and their ranges.
Auditing: DeviceLock‘s auditing capability tracks user and file activity for specified device types, ports and network resources on a local computer. It can pre-filter audit activities by user/group, by day/hour, by port/device/protocol type, by reads/writes, and by success/failure events. DeviceLock employs the standard event logging subsystem and writes audit records to a Windows Event Viewer log with GMT timestamps. Logs can be exported to many standard file formats for import into other reporting mechanisms or products. Also, audit records can be automatically collected from remote computers and centrally stored in SQL Server. Even users with local admin privileges can't edit, delete or otherwise tamper with audit logs set to transfer to DeviceLock Enterprise Server.
Shadowing: DeviceLock’s data shadowing function can be set up to mirror all data copied to external storage devices, printed, or transferred over the network and through serial and parallel ports. DeviceLock can also split ISO images produced by CD/DVD/BD burners into the original separated files upon auto-collection by the DeviceLock Enterprise Server (DLES). A full copy of the files can be saved into the SQL database or to a secure share managed by the DLES. Shadowing activities can be pre-filtered just like regular auditing to narrow down what is collected. DeviceLock’s audit and shadowing features are designed for efficient use of transmission and storage resources with stream compression, traffic shaping for quality of service (QoS), performance/quota settings, and automated optimal DLES server selection. ContentLock’s content filtering technology makes DeviceLock’s data shadowing feature even more efficient, scalable and intelligent. Content-based data shadowing is supported for all endpoint data channels including removable and plug-and-play storage devices, network communications, local synchronizations with supported smartphones and document printing. Incoming and/or outgoing transmissions can be conditionally shadowed. By pre-filtering the content of potentially large data objects before shadowing to the log, DeviceLock downsizes the streams to just those objects that contain information meaningful for post-analysis tasks like security compliance auditing, incident investigations, and cyber-forensics.
Alerting: DeviceLock provides both SNMP and SMTP based alerting capabilities driven by DeviceLock DLP endpoint events for real time notification of sensitive user activities on protected endpoints on the network.
Mobile Device Data Leakage Prevention: With DeviceLock, you can set granular access control, auditing, and shadowing rules for mobile devices that use Windows Mobile, iOS or Palm OS. You can centrally set permissions with fine granularity, defining which types of data that specified users and/or groups are allowed to synchronize between corporate PCs and their personal mobile devices, such as files, pictures, calendars, emails, tasks and notes. DeviceLock detects the presence of mobile devices attempting to access ports through USB, COM, IrDA or Bluetooth interfaces.
Network-Awareness: Administrators can define different online vs. offline security policies for the same user account. A reasonable and often necessary setting on a mobile user’s laptop, for example, is to disable WiFi when docked to the corporate network and enable it when undocked.
Removable Media Encryption Integration: DeviceLock takes an open integration approach to encryption of data uploaded to removable media. Customers have the option of using the encryption solution that best fits their security scenarios among best-of-breed technologies that include: Windows BitLocker To Go™, PGP® Whole Disk Encryption for standard FIPS-certified encryption; TrueCrypt® for free Open Source encryption; SafeDisk®, SecurStar® DriveCrypt Plus Pack Enterprise (DCPPE) software; and Lexar Media’s S1100/S3000 series USB flash drives for pre-encrypted removable media. In addition, any pre-encrypted USB media can be selectively whitelisted with usage strictly enforced. DeviceLock allows for discrete access rules for both encrypted and unencrypted partitions of such media.
Search Server: DeviceLock Search Server provides full-text searching of logged data stored on DeviceLock Enterprise Server. You can use full-text searches to find data that you cannot find by filtering data in the log viewers. The full-text search functionality is especially useful in situations when you need to search for shadow copies of documents based on their contents. DeviceLock Search Server can automatically recognize, index, search and display documents in many formats, such as: Adobe Acrobat (PDF), Ami Pro, Archives (GZIP, RAR, ZIP), Lotus 1-2-3, Microsoft Access, Microsoft Excel, Microsoft PowerPoint, Microsoft Word, Microsoft Works, OpenOffice (documents, spreadsheets and presentations), Quattro Pro, WordPerfect, WordStar and many others.
Virtual DLP for BYOD Devices: DeviceLock's Virtual DLP features provide the ability to protect any BYOD device against insider data leaks when using leading desktop and application virtualization solutions like Citrix XenApp/XenDesktop, Microsoft RDS and VMWare View. Running on a VDI Host or Terminal Server, DeviceLock "remotes" content-aware endpoint DLP policies to the securely connected BYOD device to create a virtual endpoint DLP agent that prevents uncontrolled data exchanges to local media, hosted applications and network connections of the device while "in session". This approach unifies DeviceLock DLP across physical and virtual Windows and BYOD environments.
Extended DeviceLock® Functions
Anti-keylogger: DeviceLock detects USB keyloggers and blocks keyboards connected to them. Also, DeviceLock obfuscates PS/2 keyboard input and forces PS/2 keyloggers to record garbage instead of the real keystrokes.
Monitoring: DeviceLock Enterprise Server can monitor remote computers in real-time, checking DeviceLock Service status (running or not), policy consistency and integrity. The detailed information is written to the Monitoring log. Also, it is possible to define a master policy that can be automatically applied across selected remote computers in the event that their current policies are suspected to be out-of-date or damaged.
RSoP Support: You can use the Windows standard Resultant Set of Policy snap-in to view the DeviceLock policy currently being applied, as well as to predict what policy would be applied in a given situation.
Batch Processing: Allows you to define settings for a class of similar computers with similar devices (e.g. all computers have USB ports and CD-ROMs) across a large network in a fast and consistent manner. DeviceLock Service can be automatically installed or updated on all the computers in a network using DeviceLock Enterprise Manager.
Graphical Reporting: DeviceLock can automatically generate graphical reports based on audit and shadow logs.
Permissions Report: Allows you to generate a report displaying the permissions and audit rules that have been set on all the computers across the network.
Report Plug-n-Play Devices: Allows you to generate a report displaying the USB, FireWire and PCMCIA devices currently connected to computers in the network and those that were historically connected.
Traffic Shaping: DeviceLock allows you to define bandwidth limits for sending audit and shadow logs from DeviceLock Service to DeviceLock Enterprise Server. This Quality of Service (QoS) feature helps reduce the network load.
Stream Compression: You can instruct DeviceLock to compress audit logs and shadow data pulled from endpoints by DeviceLock Enterprise Server service. Doing this decreases the size of data transfers and thus reduces the network load.
Optimal Server Selection: For optimal transfer of audit and shadow logs, DeviceLock Services can automatically choose the fastest available DeviceLock Enterprise Server from a list of available servers.
Click here for a more detailed DeviceLock overview
For more information on the DeviceLock Solution or to arrange a meeting with a Unicus representative to discuss further please email your contact details to: info@unicus-ict.co.za
|
ons.png)
ons.png)